How hundreds of websites are exposing their sensitive data and risking their user's privacy
The Purpose of this article is to show how some websites are exposing their sensitive data and risking their user's privacy. Recently some reports came out how some websites are exposing their kibana Instances due to misconfigure ElasticSearch Database so I decided to dig deeper to see how bad it can go .
In this post I will show you how easily a blackhat guy could have compromised a site, its databse, it's user's personal information.
To do this one can go to shodan.io and enter kibana port:5601 country:"US" org:"Amazon.com" in the search query
Above 5601 is the port number that you access kibana through the US is the country code for the country you want to access and Amazon.com is the services you want to discover like Azure, Google cloud, Digital Ocean, etc.
On searching above query i got 2.6k results
I checked on a random server
Below we can see a user (name hidden) logs. One can also see other details like name, address. I will not show much this is just to show how dangerous it could be for someone with privacy concerns.
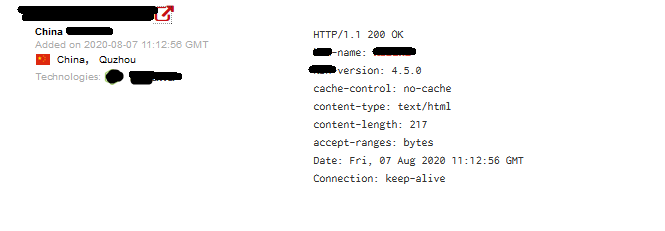
The next thing I checked was a china's database
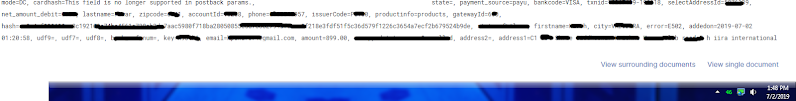
Not only china there was many companies from India, they were also exposing their user's sensitive data like below is a popular medicine store company a blackhat guy could see their user's name, IP, address, card number, password, what they have purchased from this store with their Address. He could even change it and get unauthorize access to their user's account ( at that time).
I inform them about the issue and later they fixed it ( but after taking a long time)
There was another taxi sharing website they also had the same issue
I inform them about this issue but they never replied even after 7,8 months when I checked again the issue was still there
So why does this happen?
Kibana does not have any security to enable authentication, and another reason is that people don't even set a password to their Kibana server and this leads to access to any unauthorized person to their logs with admin privileges.












Comments
Post a Comment