Check for windows Privilege escalation vulnerability
In this post we are going to see a quick and short method to check most common privilege escalation vulnerability in windows. As we know there are lot of way to do privilege escalation attack on windows if you are doing a penetration testing and for post exploitation privilege escalation is important step so that you can execute further commands.
Checking for the misconfiguartion
STEP 1. As this is a quick and short method we are going to use a tool First download the compiled version of the tool from here .
STEP 2. Now go to command prompt and type "beRoot" and then you will see what type of privilege escalation vulnerability you have .
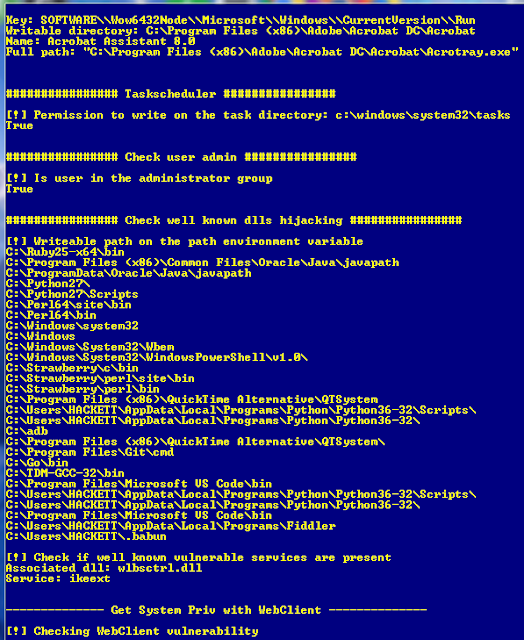
As we can see above i got multiple vulnerability and misconfiguration which can lead to privilege escalation . Some vulnerability which should be noted here is DLL hijacking which an attacker can use to inject his own malicious code into a legitimate DLL and you may not get idea if the process is malicious or not .
You can ise process Explorer to explore these types of malicious DLL file and process by looking at the parent process and cmd line of the process you can get the idea how the file executed and if the parent process is malware or not.



Comments
Post a Comment