Fileless malware Analysis with Cuckoo sandbox
What is cuckoo Sandbox
Cuckoo is a dynamic malware analysis sandbox
which is open source and completely free. We can submit any malicious binary
file and cuckoo will provide a detailed report of the malicious file,
including the behaviour of that file during execution.
What is Fileless Malware
A fileless malware is a favorite technique
for malware authors, what this type of malware does, it doesn’t write anything on
the disk to bypass mostly string base detection. The malware executes an obfuscated command usually PowerShell and during run time antivirus could not
detect the strings which are being executed and after injecting it in memory
the command get deobfuscated.
Cuckoo Interface and sample analysis
To run cuckoo just type cuckoo from
your terminal, this will start cuckoo service. Now to get the web interface
type cuckoo run webserver this will start the cuckoo web interface on
its defined URL and port address as shown below.
To submit a file for analysis, we just have
to drag and drop the malicious file or through terminal, we can type cuckoo
submit and the file path.
I have submitted a sample binary file as shown
below to see how it processes the file and what kind of behaviour analysis we
are getting.
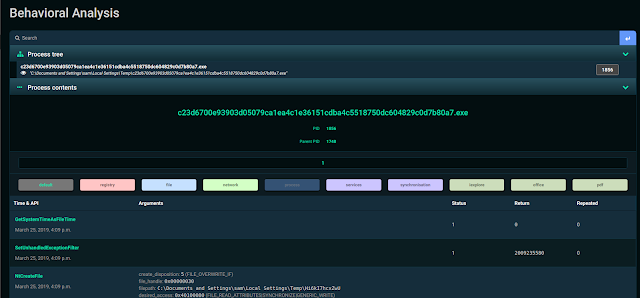
Behaviour Analysis Report
Below we can see cuckoo has given us Behaviour Report of that file. Behaviour Analysis contains Process tree which
tells what process has been created by the file during run-time, API which tells
what API is used by the file, it also gives you registry details and lots more
information which you can see in below screenshot.
Static Analysis Report
Cuckoo static analysis report gave us vast
detail of binary file, like file header info, when was the PE file compiled.
Using static analysis, we can see what memory section was accessed when the PE
file executed. We can also see the entropy of the file so that we can get the
idea if there was a packer used for the PE file. The higher the entropy higher
the chances that the binary is packed.
Static Analysis also contains the strings
command using this we can get a list of what strings are embedded in a binary
file as shown below.
All above analysis report can be checked on
the summary page, summary page shows all the analysis including screenshots,
what connection were established during run-time and much more as we can see in
below screenshot.
Analysis Of Fileless Malware
In this post we will analyze “Rozena” a
fileless malware which uses a Microsoft office icon to lure victims to open it,
but actually on clicking the file will execute an obfuscated PowerShell
command.
Below we can see a summary of the binary
file that we just submitted on cuckoo sandbox.
Above we can see the size of the file, its
hash which we can use to search on various online malware scanning sites.
Moving on in Signature section we can see
cuckoo has alerted that a hidden windows process has created. A CreateProcessinternalW performs call to
NtCreate-UserProcess to attempt creation of process in this case, it’s looks
like it is trying to create a PowerShell process here. We can see an obfuscated
PowerShell command is being executed, which is, as mentioned above is good way
to bypass string base detection.
Above we can also see that cuckoo has
indicated that this binary file has a high level of entropy that clearly
indicate this binary has used some encryption or packing method to bypass AV.
Moving on to Behaviour Analysis section we can
see API call generated by the malicious file.
It clearly shows below that an API call NtCreateFile
has generated which is used to create a new file or directory as we can see
here the binary file has created a file in %temp% folder with a filename
Hi6kI7hcxZwUI which is an executable file.
Now let’s analyse the PowerShell command the
file is executing here. Below we can see the PowerShell command is executing
during its run-time. The author has used small case and upper-case letter in
command this is the obfuscation technique used by the malware for execution as
some PowerShell variables are case insensitive.
We can also see -windowsty Hidden command
which means it will set the windows style to hidden it is used to execute
PowerShell script without showing a pop-up window. Later there is -c command
which is for command here it is executing encrypted script block as written in
bracket.
Moving on we can see below this code is
using PowerShell split, joint and convert function which will used for
decrypting the code, there is also a pipeline invoke operator this is used to
send command to invoke expression this will execute command on our the guest
machine.
Finally, on the Dropped file section we can
see the file which was dropped after creating the malicious binary. We can also
see the process responsible for dropping this file.
Final words
Apart from this cuckoo sandbox can also scan
other formats like pdf, pcap, doc and lot more malicious file format














I am very impressed with your post because this post is very beneficial for me and provide a new knowledge…
ReplyDeleteSandbox Crack