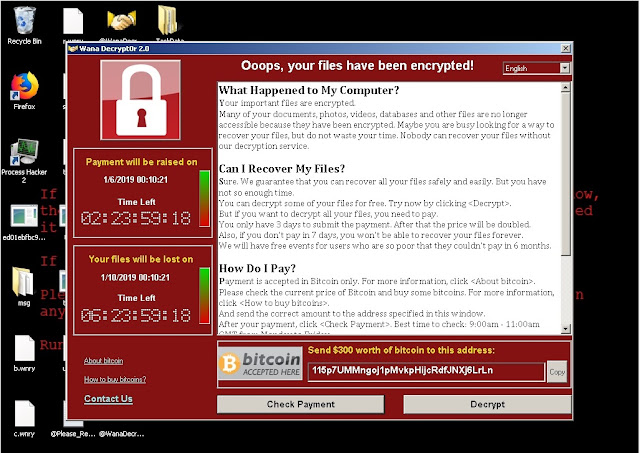
Backtrack phishing email using Open-source intelligence gathering

Recently someone sent me a spam email address and ask me for analysis to check if this email is used for any phishing or dropper. The email I got was lyuda_sereda@bk.ru , so I started with searching domain in the email on stopforumspam.com I got that this email domain has been used for a lot of malicious activity. On scrolling down I got that this email domain is associated with these malicious IP addresses used for phishing campaign Investigating on virus total I got those files with these hashes to communicate with this domain. Searching whois record of this domain shows this is from Russia Now searching on URLvoid I got that this site is listed on the blacklist domain and we can also see the server location is the Russian federation. let’s search the domain IP on cymon.io We can see this domain was also associated with a malicious PE file. So the conclusion is this email domain is mostly used for phishing campaigns and for delivering malicio