Wanacry Ransomwarwe analysis: detecting malicious network indicator and memory strings
In this post i will try to analyse wannacry Ransomware , i will try to do behavior analysis and will see what malicious network indicators we are getting , what command is it executing.
Getting the binary
Downloading the Ransomware binary file from thezoo , this repository contain binaries of lots of malwares , you can do your experiment with them in a safe environment.
Now preparing wireshark for network detection to see what DNS request it will generate on launching. Also using process hacker for deep analysis of process generating by the malware.
Now preparing wireshark for network detection to see what DNS request it will generate on launching. Also using process hacker for deep analysis of process generating by the malware.
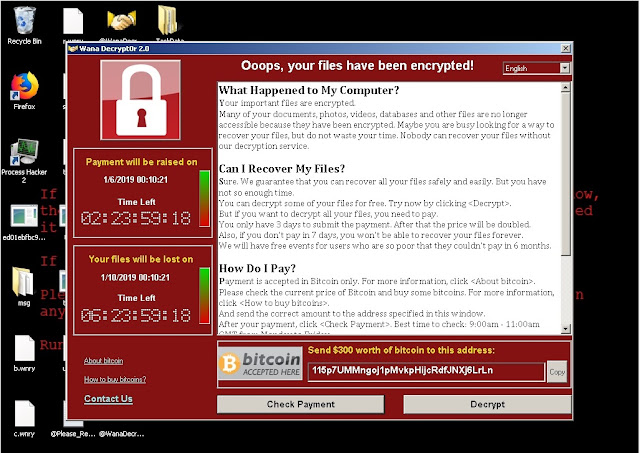
Now on launching we can see my system has been infected with the
ransomware . My files are encrypted ,desktop wallpaper changed to a
wannacry message. And a message popup on my screen giving me details
about what just happened to my system.
Going back to process hacker we can see the file with a hash.exe has started , on analysing it we can see it is executing from the desktop.
Now we will check for it's memory strings to see if we can find something interesting.
On inspecting memory string i saw a command which is executing the wanadecryptor file this is the file which just came up on my desktop after running the binary and encrypting my files.This command is also causing the file to relaunching the file again even if i terminate the process.
On further analysis of memory string we can see the message we got on the popup windows like pay message, encryption details etc.
Lets analyze the wanadecryptor file.Below we can see from command line it's executing from desktop.
On inspecting memory string we can see there are some Tor network address.
On further investigation i saw that it comes with Tor browser in it, as we saw above we can say it will try to communicate to other services through tor network which is necessary to hide your identity.
Now i will click on check payment options and will see what's happening on network side.
Above we can see it's trying to communicate to it's server , so let's go back to wireshark and see what's happening on network side.
Here we can clearly see it's a TCP handshake process which means it's trying to communicate to a server which we can see here is 37.187.21.11. So let's check what's this IP address and what's it's reputation.
On checking virustotal we can see above that those domain name resolve to this IP address which they can't connect to as this server is down by now. Below that we can see the file names which is communicating to this server , so we can clearly add these network address and binary files to our blacklist.
Now let's investigate taskhsvc process which is associated with the wanadecryptor.
Above we can see it's parent process is WanaDecryptor looks like this binary has come with the malware (the file with zip in wanadecrypt memory string) for creating Tor connection and to communicate with it's server.
Now by looking at it's memory we can see below lot's of IP address and tor address which looks like malicious network indicator .
Now i will filter out all the IPs using regular expression , i am using cyberchef for this which is a web app encryption, encoding, compression and data analysis.
Now going back to the list and filtering out all the IPs.
we got all the IP address , we can save this list and add them to our blacklist of our firewall or IPS systems.
So this was the analysis of the wannacry Ransomware to detect malicious behavior,network indicator, execution.
Going back to process hacker we can see the file with a hash.exe has started , on analysing it we can see it is executing from the desktop.
Now we will check for it's memory strings to see if we can find something interesting.
On inspecting memory string i saw a command which is executing the wanadecryptor file this is the file which just came up on my desktop after running the binary and encrypting my files.This command is also causing the file to relaunching the file again even if i terminate the process.
On further analysis of memory string we can see the message we got on the popup windows like pay message, encryption details etc.
Lets analyze the wanadecryptor file.Below we can see from command line it's executing from desktop.
On inspecting memory string we can see there are some Tor network address.
On further investigation i saw that it comes with Tor browser in it, as we saw above we can say it will try to communicate to other services through tor network which is necessary to hide your identity.
Now i will click on check payment options and will see what's happening on network side.
Above we can see it's trying to communicate to it's server , so let's go back to wireshark and see what's happening on network side.
Here we can clearly see it's a TCP handshake process which means it's trying to communicate to a server which we can see here is 37.187.21.11. So let's check what's this IP address and what's it's reputation.
On checking virustotal we can see above that those domain name resolve to this IP address which they can't connect to as this server is down by now. Below that we can see the file names which is communicating to this server , so we can clearly add these network address and binary files to our blacklist.
Now let's investigate taskhsvc process which is associated with the wanadecryptor.
Above we can see it's parent process is WanaDecryptor looks like this binary has come with the malware (the file with zip in wanadecrypt memory string) for creating Tor connection and to communicate with it's server.
Now by looking at it's memory we can see below lot's of IP address and tor address which looks like malicious network indicator .
Now i will filter out all the IPs using regular expression , i am using cyberchef for this which is a web app encryption, encoding, compression and data analysis.
Now going back to the list and filtering out all the IPs.
we got all the IP address , we can save this list and add them to our blacklist of our firewall or IPS systems.
So this was the analysis of the wannacry Ransomware to detect malicious behavior,network indicator, execution.
Resource And Tools use
Process Hacker.
Registry explorer from Windows sysinternals.
Procmon




















Comments
Post a Comment