Parent process spoofing and how to detect them
Malware uses vaious
techniques to hide it or evade from antivirus or EDR system. So I
decided to discuss about a very intresting malware hiding technique
Parent process spoofing. This technique is well discussed by many other
infosec people and Didier Stevens blogged about this in 2009. I decided to discuss in layman form.
parent process spoofing technique allows a malicious program to spawn a process of its choice. It helps the malicious program to hide itself from the parent-child process analyzing which helps defender to find anomalies.
How Does It work
This is an abuse of windows feature It uses a Windows API CreatProcessA function which use to create a new process. This function has a parameter lpStartupinfo which allows you to choose the parent process.
lpStartupinfo points to STARTUPINFOEX structure
The STARTUPINFOEX structure contains lpAttributeList
lpAttributelist is created by InitializeProcThreadAttributeList function this function will allocate the memory required for the attribute list and then initial it.
Finally, the UpdateProcThreadAttribute function sets the parent process and the process gets execute by CreateProcessA function.
Demo Time
There are lots of open source code for this demo.I chose c_shot for this demo. This will download the malicious file from remote location end execute it straight into memory. This can help us to evade some antivirus.
Prepare the stageless payload this will contain everything to start a listener so no stager required and a secure communication.
Start the listener
Host the payload on the attacker machine
Now go to the victim machine and execute the command. This command will download the .bin file and execute the shellcode into the child process with our spoofed parent process. For example, here explorer.exe is my parent process and notepad is the child process.
And I Got the shell
Investigate the malware
If we look at notepad we can see it's showing the parent process in explorer.exe
But looking at the notepad process memory we can see it has PAGE_EXECUTE_READWRITE permission for a private working set and that's a red flag for any malware hunters.
By looking at the call stack between two notepad process one is executed by a legit parent and one is executed by a spoofed parent we can see the entry of 0x000000 in the malicious process stack. On the other side, there is an entry of win32.dll USER32.dll then notepad.exe clearly says this process was not created by any malicious process and another one is injected.
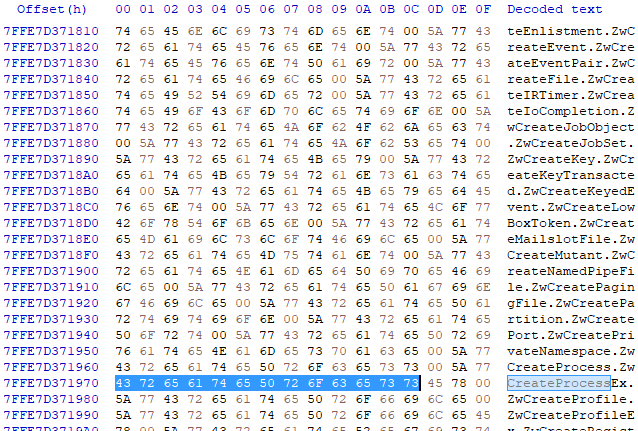
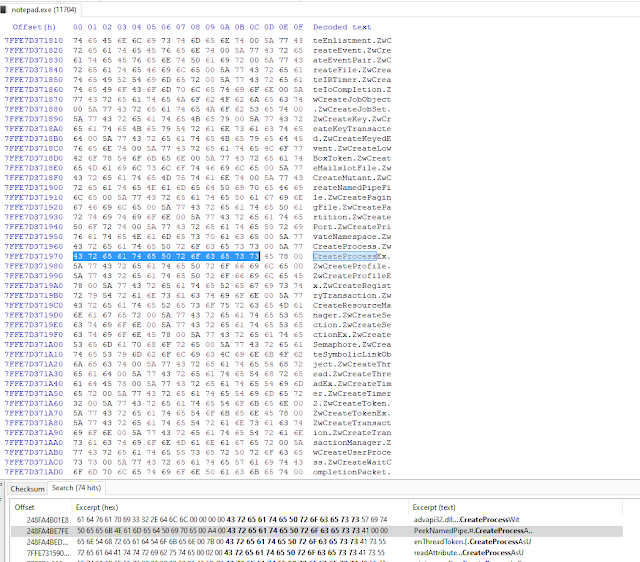
Checking the process in hxd I search for some of those functions which the malware used to create spoof parent process
Above we can see this process has CreateProcessA function and below I got search result for
UpdateProcThreadAttribute which set the parent process
I also looked at tcpview and it shows notepad.exe was communicating with our attacking machine
For automated hunting, I used detect ppid-spoofing this script used FireEye pywintrace python library for detecting spoofed parent process
And it immediately detected that spoofed parent process
Refrence
https://docs.microsoft.com/en-us/windows/win32/api/winbase/ns-winbase-startupinfoexa
https://blog.f-secure.com/detecting-parent-pid-spoofing/

















Comments
Post a Comment