Basic Vulnerability Assessment and Penetration Testing of a Website
site is using, we can see below this site is using WordPress as CMS, Apache web server running on
Ubuntu.
After checking on http://wappalyzer.com we can confirm above discovery. We got lots more details
about running services on this site.
Enumerating web application firewall
Before going any further, we should first confirm if the site’s using any firewall or not, so we can
decide how many threads or request to send before it block our access. For this I am gonna use
wafw00f as shown below.
decide how many threads or request to send before it block our access. For this I am gonna use
wafw00f as shown below.
So it’s confirm this site is not using any web app firewall now we can move ahead in our assessment.
Exploiting XML-RPC API
Many WordPress sites are vulnerable to xmlprc brute-force attack. A bad guy can use brute-force attack against the target site. We can see xmlrpc is available by going digitalfobot.com/xmlrpc.php directory.
We can use Metasploit module for brute-force attack for this. As we can see below the exploit has
successfully run and we can brute-force the target for available username and password.
successfully run and we can brute-force the target for available username and password.
But I will use wpforce as this is much faster than Metasploit. I will use rockyou.txt word list for this.
An attacker can also use password profiling against the target for dictionary attack which has a better success rate.
An attacker can also use password profiling against the target for dictionary attack which has a better success rate.
We can see in both cases, it’s confirmed we can successfully launch a brute-force attack against the
target even it’s Metasploit or wpforce (wpforce gave us faster brute-force rate than Metasploit).
target even it’s Metasploit or wpforce (wpforce gave us faster brute-force rate than Metasploit).
Enumerating vulnerable plugins
A WordPress site can contain many vulnerable plugins , a pentester also should look for available
plugins and should also check if it’s vulnerable or not. In this case we can see below this site it using Elementor plugin.
Searching on searchsploit didn’t give us any available exploit for this plugin.
Now let’s see if it is vulnerable or not using wpscan (we can also use this for enumerating available
plugins)
After enumeration we can see below this plugin is vulnerable, which give authority to non admin
logged in user access to specific back-end function.
Now let’s see if it is vulnerable or not using wpscan (we can also use this for enumerating available
plugins)
After enumeration we can see below this plugin is vulnerable, which give authority to non admin
logged in user access to specific back-end function.
Enumerating vulnerable services
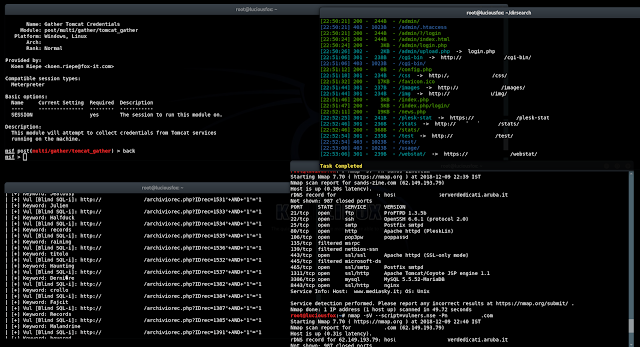
Now let’s see if there are any outdated or vulnerable services on this site. There are lots of ways for this like using service detection on nmap, but this could take time so I am going to use an nmap script
“nmap-vulners” for this.
“nmap-vulners” for this.
And below we can see all the vulnerable services with their CVE details. All vulnerabilities has been
arranged on a rank basis. Most critical vulnerability is on top.
arranged on a rank basis. Most critical vulnerability is on top.
Now I can use Google dork to search available exploit for these vulnerabilities as shown below. So first lets check on GitHub for this.
And we got an exploit on GitHub
You can replace site with your desire website URL















Comments
Post a Comment